select the best answer. which of the following are breach prevention best practices
The employees play an essential responsibility in keeping their. Access only the minimum amount of PHIpersonally identifiable information PII necessary B.
Board Oversight Of Cyber Risks And Cybersecurity
The following best practices may help.

. It is better to acknowledge that data breaches are inevitable than to assume your organization is. In the age of digital data keeping information safe is more important than ever. Select the best answer.
There are steps and practices that you can implement for breach prevention. Which of the following are breach prevention best practices. 7 Key Steps To Investigate A Data Breach With Checklist Ekran.
1 who has lead responsibility. Which of the following are breach prevention best practices. Access only the minimum amount of.
Endpoint breach prevention is needed not only to fulfill legal requirements but for the issues well in the next section we are going to cover best practices which are needed to. Train Employees on Security Awareness. Select the best answer.
Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your. Promptly retrieve documents containing PHIPHI. Promptly retrieve documents containing PHIPHI from the printer.
Which of the following are breach prevention best practices. Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the. Which of the following are breach prevention best.
Developing the IRP will help the IT staff of the company to control the data breach incidents. What are breach prevention best practices. Logoff or lock your workstation when it is unattended.
See answer 1 Best Answer. Best practices for breach prevent are. Endpoint breach prevention is needed not only to fulfill legal requirements but for the issues well in the next section we are going to cover best practices which are needed to.
Making weak passwords can be a reason for Data. 30 Best Practices for Preventing a Data Breach. Physical measures including policies and procedures that are used to protect electronic information systems and related buildings and equipment from natural and environmental.
All of this above Best practices for breach prevent are. Top 4 Human Errors In Cyber Security How To Prevent. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
D communicating a purchase order to a supplier. Create Strong Policies Strong Passwords. Select the best answer.
Identify areas that store transmit collect or process. Which of the following are breach prevention best practices Saturday June 11 2022 Edit. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best.
Identity sensitive data collected stored transmitted or processes. Which of the following are breach. All of this above.

Cybersecurity Best Practices For 2022 15 Data Protection Methods Ekran System

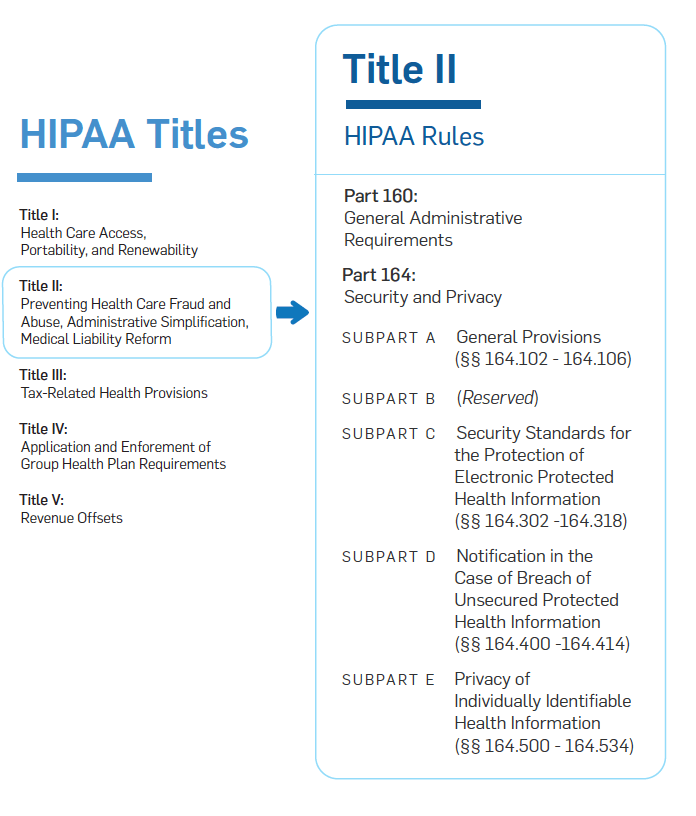
Securitymetrics Guide To Hipaa Compliance

Breach Prevention 5 Best Practices To Protect Your Data Mro Corp

Top 20 Docker Security Best Practices Ultimate Guide

Which Of The Following Are Breach Prevention Best Practices Public Health

Software Data Breach Overview Veracode

Product Best Practices Archives Rfpio

How To Choose The Best Password Manager Avast
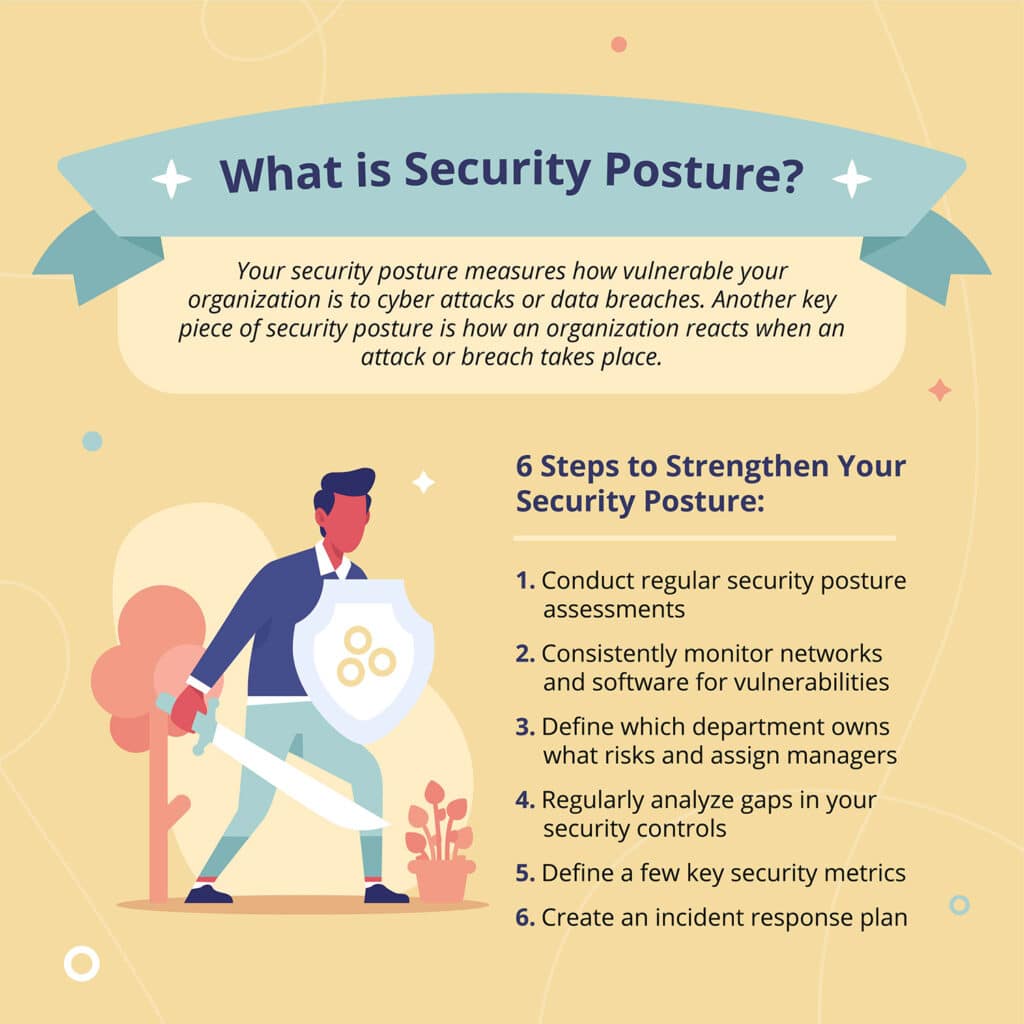
6 Steps To Strengthen Your Security Posture Hyperproof

Data Breach Prevention Mimecast

5 Critical Pieces Of A Good Security Playbook Axcient

Information Security Wikipedia

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

Which Of The Following Are Breach Prevention Best Practices Public Health

Data Breaches 101 How They Happen What Gets Stolen And Where It All Goes Security News
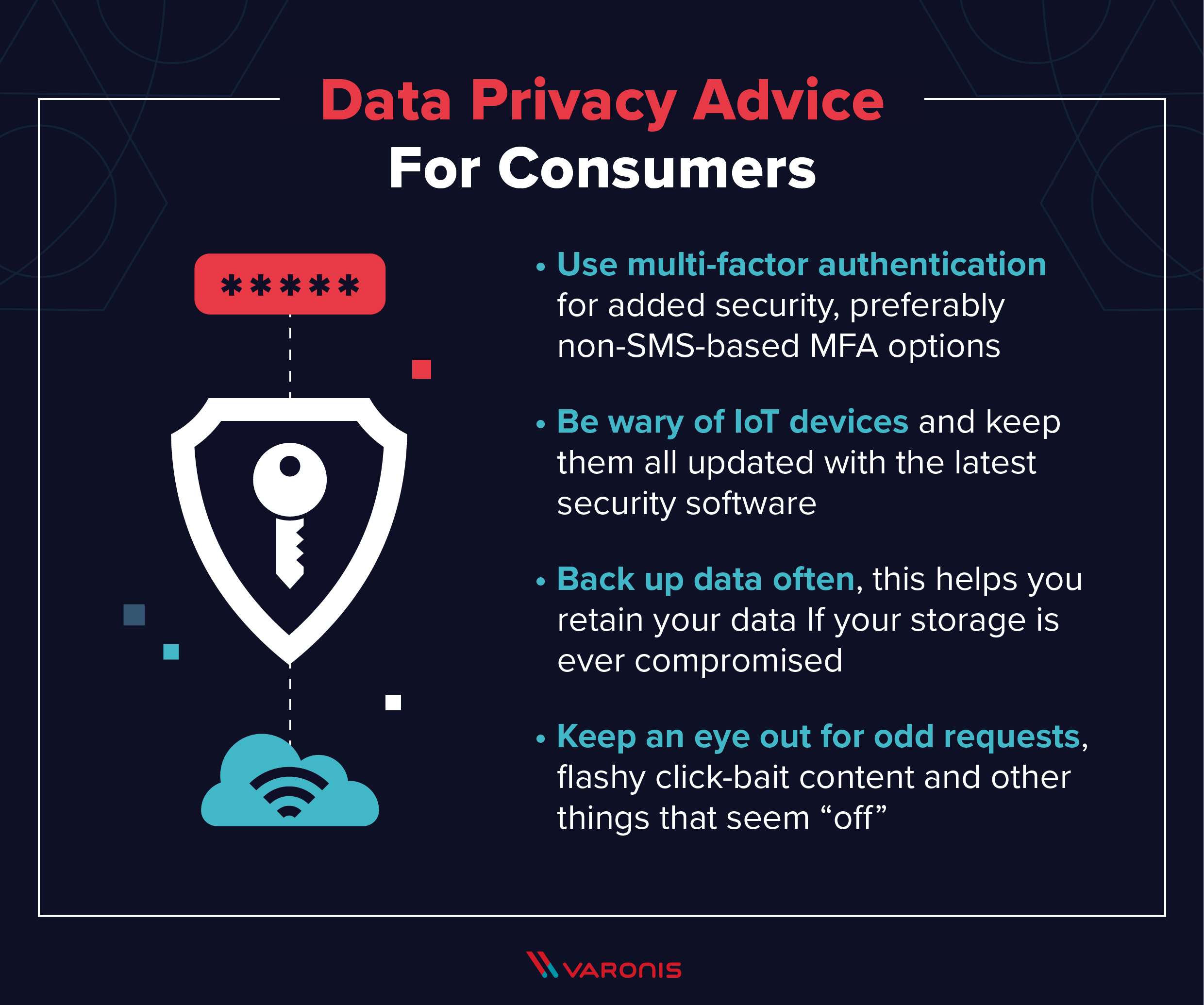
Data Privacy Guide Definitions Explanations And Legislation